Blog
Passwordless Authentication: It’s Time to Stop Using Passwords
If you think that passwords are one of the fundamental pillars of modern security, then you’re absolutely correct. The problem is that this pillar is so full of cracks and other structural weaknesses that even a small gust of wind can send it tumbling to pieces....
Facts Are In: Small Businesses Are Now the Top Target of Cyberattacks
It’s true that we only hear about cybersecurity issues when they’re happening to big companies—like when Colonial Pipeline was hacked in May making both the national and local newspapers, and when a hacker recently stole more than 50 million customer records from...
Don’t Make These IT Mistakes as You Grow
We routinely come across small businesses who aren’t happy with the how their IT shaped up over the years. They feel their IT investments never really showed the kind of returns that they expected, and they come to us hoping that we can change that trend. As a part of...
Understanding Social Media Impersonation Attacks (and what to do about them)
Does your company have any social media profiles? It should. Even for strictly Business to Business (B2B) companies, LinkedIn should be kept up with at a minimum (and here’s why). But just like everything else in the IT world, benefits always come with risk. So...
7 Common Password Mistakes to Avoid (and Their Solutions)
According to the Verizon 2021 Data Breach Investigations Report, credentials are the #1 way that a cybercriminal hack into an organization, with 61% of breaches attributed to leveraged credentials. That means that by way of clone phishing, domain spoofing or one of...
Help Desk Cavalry on 2021 Inc 5000 Fastest Growing Companies in America List
Help Desk Cavalry Listed as One of Only Four WA State Information and Communications Technology (ICT) Businesses to Be Honored on the Inc Magazine’s Inc 5000 Fastest Growing Private Companies in America 2021 List Help Desk Cavalry celebrates its second consecutive...
Is Remote Work Too Much of a Cybersecurity Risk?
Even if your company has already adopted remote work (or hybrid work, as in some on-site and some remote) as a standard method, this question has probably crossed your mind. Maybe it still is. Kudos to you and your team for taking the security risks seriously and for...
How to Protect Smartphones from Cyber Threats
Not that long ago, you would be happy if your mobile phone had enough memory to store 100 contacts, and you would be ecstatic if it could also store the same number of text messages. Today, your smartphone can not only store a virtually infinite number of contacts and...
How to Prioritize Employee Experience (ESAT) While Keeping Your IT Costs Down
Modern organizations need their technology to be just that: modern. And that also means that they need modern ways of working to be productive and competitive. Last year’s work routine upheaval (hello, barking dogs and curious toddlers) led to pretty much everyone...
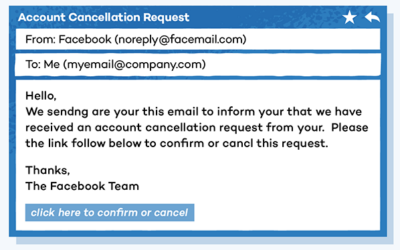
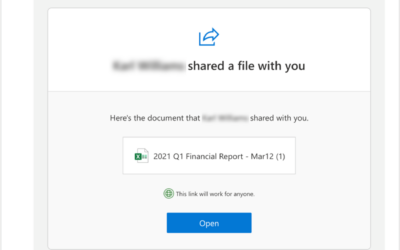
New phishing method discovered: Consent Phishing
A new phishing method has recently been identified and is now on the rise. And because of its well-crafted mimicking abilities, it’s hitting small business end users at an increasing rate. Consent phishing is a new technique that attackers are using in response to the...
Tips on Cybersecurity Employee Training
Of all the cybersecurity tools, tricks, software, and processes, none is more important than employee training. It must always be at the heart of your cybersecurity plan. That’s because no amount of cutting-edge technology can protect you from the one thing that is...
5 Ways You Can Improve Your Search Rankings (SEO)
These days every company knows the acronym “SEO”, but for most, the real story behind improving it remains a mystery. While there’s no real shortcut to high rankings on web searches, there are a few quick fixes to get (and keep) your site’s content optimized so you...
Data Security Requirements That Every Small Business Should Know
Data security is a big deal, and as you may have seen recently in the news, it’s a big deal that just keeps getting bigger. The most startling fact is that attacks are more common in the small business arena than in any other. That’s because small businesses typically...
Tips for Using Core Technology to Grow a Small Business
Growing a small business requires a lot of dedication, hard work, and strategic planning. It also requires creativity and outside-the-box thinking when leveraging core technology to its full potential. We should be clear here that by “core” we mean the essential...
5 Reasons Why Even the Smallest Businesses Need LinkedIn
LinkedIn has been around for almost 20 years and is the leading business networking and information sharing site in the world. Even now, many small businesses still regard it as a “corporate tool” or something that a hopeful event speaker spends all day on to connect...
Demystifying What Digital Transformation Means for Small Business
All small business owners understand that change is inevitable. After all, finding a horse carriage repair shop is now somewhat more difficult than it was just 100 years ago. But when change happens so quickly that the term “transformation” becomes more appropriate,...
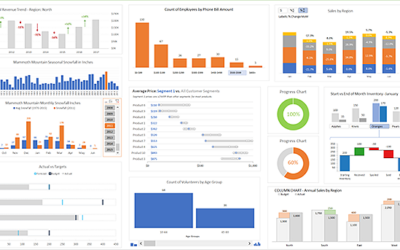
How to Create Professional Charts in Microsoft Excel
The human mind is wired to create stories from pictures which is why charts are one of the quickest ways to communicate the narratives that data can tell. Very few people actually enjoy staring at raw 1’s and 0’s, and most need at least a little guidance to help them...
5 Biggest IT Management Challenges in 2021 (so far)
It’s been more than a year since the pandemic drastically upended small business IT plans, forcing organizations to improvise as they tried to remain operational under uncertain conditions. And while some parts of the world are finally returning back to normal after...
Small Business Takeaways from the Recent Colonial Pipeline Data Breach
You’ve probably seen a bit about the $5M ransomware attack that hit Colonial Pipeline Co., the largest pipeline system for refined oil products in the US. As a quick recap, the oil giant’s network was breached by hackers who encrypted their systems and demanded a...
3 Ways Employees Can Compromise Your Security (and How to Prevent Them)
Even if you’ve already implemented a state-of-the-art firewall, antivirus software, and every other element of modern cybersecurity, there’s a chance that your defenses could be compromised at any moment. That’s because no one can fully defend their data and their...
Communicating Clearly: Email vs IM vs Phone
Having options is great, but not everyone uses the same communication tools in the same ways. If you’ve ever received a two-word email that didn’t address your questions, or an instant message that was more like the first chapter of a novel, then you’ve experienced...
Hiring Employees Effectively in the Age of Remote Work
Employees in every corner of the nation are finally returning to their offices, but the global shift to remote work continues. Here’s a WOW statistic: According to data published by Upwork, 36.2 million Americans will be working remotely by 2025. That’s an 87%...
Why It’s Critical That Small Businesses Modernize Their Customer Experience
Technology has evolved in leaps and bounds through the decades, and customers’ expectations have evolved with it. Empowered by their always-connected electronic devices, modern customers are used to personalized services available through multiple convenient channels,...
How to Safely Disinfect Your Technology Equipment
Since cleaning and disinfecting have become a priority for most of us in the pandemic era, safety-minded tech users occasionally ask us “how do I make sure my hardware is safely disinfected?” Basically, they want to know how to clean it quickly and reliably without...