Does your company have any social media profiles? It should. Even for strictly Business to Business (B2B) companies, LinkedIn should be kept up with at a minimum (and here’s why). But just like everything else in the IT world, benefits always come with risk. So unfortunately, something as innocent as keeping a company profile updated can be exploited. Here’s a look at how, as well as a handful of tips on how to avoid becoming a victim.
What Are Social Media Impersonation Attacks?
Impersonation attacks aren’t new. All types of fraud have been around long before Kevin Mitnick (who some would argue is the Father of Hacking) made social engineering famous. But phishing is perhaps the best-known method of impersonation attack, relying on cleverly crafted emails to give the impression that the sender is a known and trusted person.
To be a successful email phisher, cybercriminals must win multiple fights before they even get to the big battle of convincing a worker that they should share information. That’s because most organizations these days use real-time phishing protection to stop the evil-doing email messages from reaching employee inboxes. Even more effective is that many companies are now training their employees on how to detect phishing emails, so it often takes many unsuccessful attempts before the attacker actually makes contact. All of this makes email phishing one of the most time-consuming methods. So, since most cybercrime is all about a quick payday, the criminals turn to other methods to fight their way into a network.
Enter social media. Facebook, Twitter, Instagram, and even LinkedIn offer a variety of ways get to both personal and professional data that can lead to a hack. And they actually make for better attack locations than in a professional mailbox because these arenas are outside of the usual work sphere, so there’s a higher likelihood that potential victims aren’t wearing their armor.
Main Types of Social Media Impersonation
Social media impersonation attacks can be broadly grouped into two main categories:
Employee Impersonation Attacks
Anyone can be anything on social media, so it’s fairly easy for cybercriminals to impersonate individual employees. Ann Lewis, Senior Advisor for Technology Delivery at the SBA, wrote about what it’s like to be on the receiving end of a social media impersonation attack on Medium, and there are many lessons to be learned from her experience. The biggest one is that social media users accept friend requests without much scrutiny, and they certainly don’t pay the same attention to usernames as they do to email addresses.
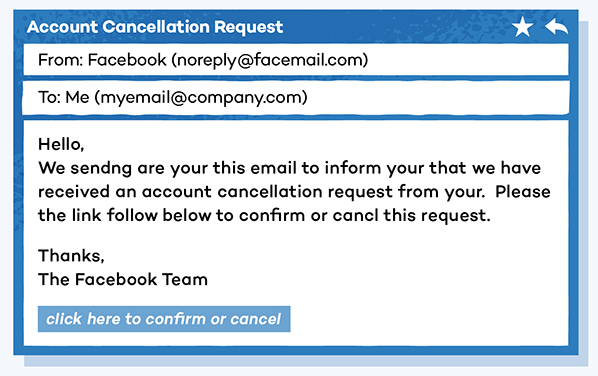
Brand Impersonation Attacks
Virtually all popular brands and many small and medium-sized businesses have at least some social media presence these days. Cybercriminals can take advantage of this in two distinct ways. First, they pose as brands to get sensitive information from customers. Second, they create fake social media accounts that impersonate legitimate organizations to spread misinformation, sell fake products, distribute malware (which incidentally could wind up on company’s entire network if the victim is on a work machine), and more.
How to Address Social Media Impersonation Attacks?
Just like social media itself, impersonation attacks are here to stay. So the best tactic is to learn about it (kudos to you, dear reader), stay up on trends, and familiar with ways to avoid being a victim.
The good news is that keeping your company safe from social media impersonation attacks—at least to some extent—is pretty easy and most don’t cost you a dime.
- Document your social media presence: To be able to defend yourself, you need to know what you’re defending, so start by mapping your organization’s social media footprint, including which platforms you use and which individuals have admin access and which employees are connected to them.
- Verify your social media accounts: Many social media networks allow companies to verify their accounts, so they can let users know that their accounts are authentic and trustworthy. If you see this option, take it. And don’t hesitate to remind your customers to trust only your account.
- Sign up for social media monitoring: There are companies who monitor social media networks to detect an impersonation attempt and address it before it’s too late to do anything. The cost of social media monitoring is always far easier to swallow than the cost of even a relatively minor cybersecurity incident.
- Educate employees: Social engineering attacks wouldn’t be nearly as effective as they are if users were more aware of them and knew how to protect themselves. For example, you need to teach your employees to enable multi-factor authentication whenever possible and think twice before accepting any friend request. Training is a must.
- Update your incident response plan: The more prepared you are for the worst-case scenario, the easier it will be to reduce its impact. Imagine how your organization could be affected by various social media impersonation attacks and update your incident response plan accordingly so that you can react swiftly and confidently.
Don’t have an incident response plan? Unsure how to effectively train your employees? Just contact us. We help companies establish policies and plans (and yes, train their employees) for every type of scam and attack that are out there. Just let us know how we can help.