A new phishing method has recently been identified and is now on the rise. And because of its well-crafted mimicking abilities, it’s hitting small business end users at an increasing rate. Consent phishing is a new technique that attackers are using in response to the rise of end users enabling Multi-factor Authentication (aka MFA or 2FA). Consent phishing is particularly effective because it doesn’t bear the red flags that many of the longer-standing methods raise. However, there are practical ways to reduce your risk.
If you don’t have MFA/2FA enabled for your systems, you’ve probably still heard about it. More and more platforms are adding support for MFA—even requiring it in some cases—and users everywhere are adopting it to secure their accounts. As is the constant in cybersecurity, attackers are adapting to figure out new ways to exploit vulnerabilities which (just like in the case of many other types of phishing attacks) come down to human error.
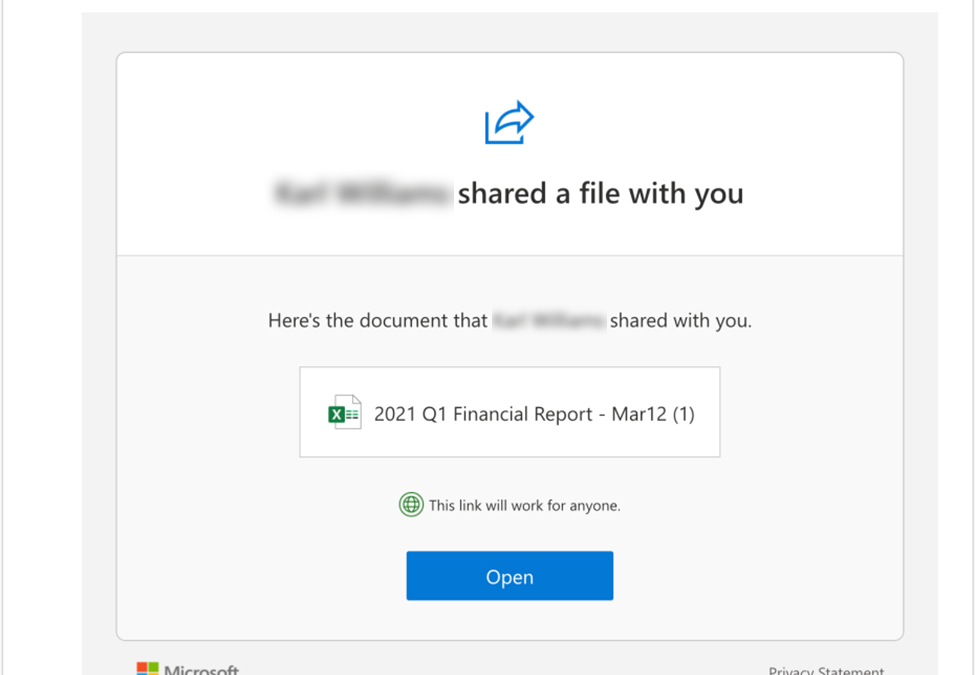
Imagine it’s Monday morning and you’re still waiting for the effects of coffee to kick in as you open your email to see that a colleague shared a financial report with you.
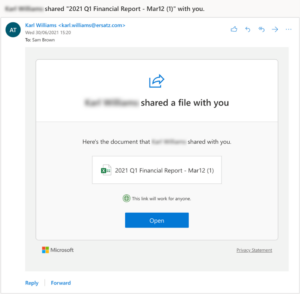
You want another cup of coffee and you knew a report was heading your way soon, so you decide to click the link that looks just like the “Yes give me access” prompt you’ve clicked through a thousand times. While your emails are piling up, you see that it’s a microsoftonline.com domain, it’s an https URL, and there’s a green tick in the corner so you make the hurried assumption that everything looks fine. Then you make another cup of coffee while it loads.

If you’d taken the time to look closely, then you’d see that this prompt is in fact asking you to approve access rather than granting you access. But with your muscle memory in full control, you click “Accept” before even glancing at the screen. You wait for the spreadsheet to open but are presented with a generic “File does not exist” error page. You figure you’ll just reach out to your colleague later after you have your email under control. You make a quick reminder, then get to work.
BOOM. You’ve been consent phished. You’ve just granted the attackers permanent access to your account. Permanent as in they will retain access even if you change your password or have MFA enabled. Chances are the attacker’s tools will immediately start downloading every piece of data you just granted them access to, which they can then comb for personal and banking information whenever they want.
For a lot of people reading this article, it may seem obvious that you need to audit the apps that you’ve approved. Something that everyone is doing regularly, right? The reality though (Monday mornings, too little coffee, assumptions about what’s heading your way) this isn’t something that most people check. Users appreciate that the prompts the software manufacturers have created are designed to be as seamless as possible and not to get in their way. But the downside is that we are desensitized to the flow, text, and icons that appear regularly, so most mimics can run right by them.
TIP: If this has piqued your interest, you can check what access you have personally granted on Google Workspace and Microsoft 365.
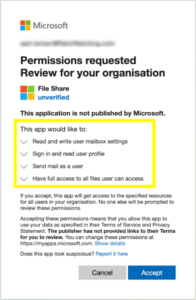
In this scenario, you’ll probably see that by clicking “Accept” you granted some pretty serious permissions here. These permissions allow the attackers to read and write any files that you have access to, and they could download these files and then delete them. You also granted permissions for the attackers to send emails as you. They’re now able to pose as you and send phishing or social engineering emails to your colleagues. And finally, you allowed them to edit your Outlook settings which they could use to create Outlook Rules—like forwarding to themselves—so your account is busy working for them behind the scenes without them ever having to login.
What you can do to avoid being a victim
Unfortunately, the only fool-proof method to prevent this kind of attack is not one that any modern, productive company would want to employ. You’d basically have to stop users from granting access to third party apps, which means that they can’t use basic business tools. As you can imagine, this would slow productivity down to a crawl.
A more balanced approach is to let users find and request apps, but have administrators approve the apps. More and more platforms (including Microsoft 365) are offering built-in “admin consent” workflows that ensure a second pair of eyes can confirm the approval. You can also make it even easier for users by pre-approving widely used apps from trusted publishers and users won’t even notice there is new protection in place 99% of the time.
Consent phishing is still an emerging technique, and we believe that it has not reached peak usage by attackers yet. We’re constantly monitoring new threats and watching their trends. We work with industry-leading security partners who constantly innovate both their software and hardware so known threats can always be met head-on. On top of that, we have full-scale phishing training and testing programs for your end users which can cover almost any scenario. Just be in touch if you’d like to know more. And don’t forget to like us on Facebook or follow us on Twitter to get updates about cybersecurity threats, new and old.