Blog
IT Considerations When Hiring Seasonal Staff
For companies with seasonal spikes, like accounting firms at tax time or retail stores during Christmas, hiring a part-time, temporary workforce is a natural part of annual operations. While this works well for handling labor costs, it can pose some real challenges...
What to Consider Before Allowing Employees to Bring Their Own Devices (BYOD)
By this point, it’s common knowledge: “Bring Your Own Device” isn’t a trend, it’s the future. Workplaces that allow personal devices are the new normal which means that a BYOD policy attracts new hires, and it also lifts employee morale and productivity. But this...
Why Employees Love Using Their Own Devices (BYOD)
Bring Your Own Device (BYOD) to work was just an idea a few years ago but it’s now becoming the norm. For most people (including those reading this article) using your personal smartphone, tablet, or laptop for work seems natural. The downside is that employees are...
How to Build a Small Business Cybersecurity Compliance Plan
In our digital business era, cybersecurity incidents are now a fact of doing business. No matter how small a business is, they all now face a myriad of threats that can seriously jeopardize their ability to remain operational. Which is why it’s so critical for small...
7 Tips for Creating (and Maintaining) a Great Small Business Privacy Policy
Please note that in no way is Help Desk Cavalry providing legal information or counseling in this article. The content below is offered for your information only and any concerns or questions about complying with current laws should be directed to a legal...
Cybersecurity Compliance Is Coming for Small Businesses
From time to time, businesses of all sizes face an unstoppable force of change. Sometimes, this force comes suddenly like an earthquake and reshapes the entire business landscape—just like the COVID-19 pandemic did in 2020. More commonly, however, the force begins as...
What Should a Small Business Privacy Policy Cover?
Please note that in no way is Help Desk Cavalry providing legal information or counseling in this article. The content below is offered for your information only and any concerns or questions about complying with current laws should be directed to a legal...
What Is a Small Business Privacy Policy and Why Do I Need One
Please note that in no way is Help Desk Cavalry providing legal information or counseling in this article. The content below is offered for your information only and any concerns or questions about complying with current laws should be directed to a legal...
5 Ways Small Businesses Can Save Money on Security
Small to medium-sized businesses and large enterprises may seem worlds apart, but they deal with many of the same cyber-security threats. That’s because in recent years, cybercriminals are increasingly targeting small businesses because they’re easy marks. It’s no...
Cybersecurity Compliance Can Be a Competitive Edge for Small Businesses
For small businesses, the most common competitive advantage is their proximity to customers, which allows them to deliver a more personalized customer service experience. But there’s another often-overlooked source of a competitive advantage that small businesses can...
Why You Should Care if Your Employee’s Personal Social Media Account Was Hacked
Personal social media accounts are one of the most common forums for cyberattacks. You may think cybercriminals would prefer to hack online banking accounts or shopping accounts, but that doesn’t seem to be the case. Social media accounts hold a lot of personal...
Multi-Factor Authentication (MFA or 2FA) 101
There’s a very good chance that you’re already using multi-factor authentication somewhere in your virtual life. That’s because it’s one of the fastest, cheapest, and most universal way for companies and manufacturers to enforce safety protocols for those logging into...
Top Cybersecurity Compliance Considerations for Small Businesses in 2022
Cybersecurity compliance is like a puzzle. To see the big picture for your company, you must place all of the pieces in the right place. The problem is that it’s not immediately obvious how many pieces there are. Unfortunately, regulations aren’t delivered to small...
The Ultimate IT Checklist for Evolving Small Businesses
Many small businesses begin with simple basics: a plan for administration, sales, technology, customer service, and maybe some marketing. Of all of these, technology is quickest to change while also carrying the highest risk. As companies grow, though, they often...
Small Businesses Outside of California Can’t Afford to Ignore the California Consumer Privacy Act (CCPA)
Please note that in no way is Help Desk Cavalry providing legal information or counseling in this article. The content below is offered for your information only and any concerns or questions about complying with current laws should be directed to a legal...
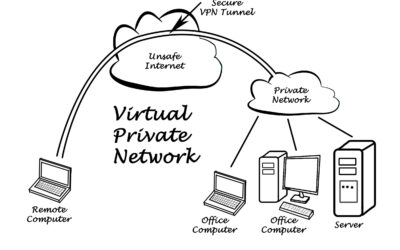
VPN 101: Remote Access and Safety
For many of us, working outside the office walls is now “business as usual”. One of the many upsides to this is that technology is now catching up—and getting more competitive—with the tools needed to optimize working remotely. The advantage is in this is that there...
Six Reasons You Need a Password Management System ASAP
When it comes to workers organizing and managing their business passwords, we’ve seen everything—from the office admin who has the QuickBooks password post-it-noted to her monitor to the company owner who relies on his assistant to text him passwords when he needs...
Top Keyboard Shortcuts that Work Across Chrome, Safari, Firefox, Edge, and More
These days, most computer workers rely on the internet for everything from accessing necessary systems to researching the cheapest keyboard replacement. A big time saver is knowing how to speed around your favorite web browser using keyboard shortcuts. Enjoy! Basic...
Why Cybersecurity Compliance Is Becoming Increasingly Important for Small Business
Even the smallest business must play by certain rules to avoid legal issues. From hanging labor law posters to filling taxes on the scheduled IRS and state deadlines, these rules are now so common that most companies simply take them for granted as the activities...
Why IT Must Know Before Employee Onboarding or Offboarding
Typically, businesses pay the most attention to security while employees are working with their data, like password hygiene, software account management, and network access. But these same companies often leave out two of the most important moments in an employee’s...
How to Optimize Device Deployment
Today’s small businesses usually have to rely on a mix of both personal and professional devices to make sure their employees have all the access they need when they need it. But safely deploying and managing desktop computers, laptops, smartphones, and tablets is a...
5 Things to Consider When Looking for New Software
These days, every small business needs software of some kind, whether it lives on a local server in an air conditioned closet or virtually in the Cloud. These software programs range across everything an organization needs to keep running, including accounting,...
Third-Party Data Breaches Are a Growing Problem for Small Businesses
Many small businesses are still struggling with cybersecurity best practices when securing their own networks, and it’s easy to see why: Dangerous threats seem to be multiplying every day, and the complexity of modern networks is growing as well. Honestly, it’s enough...
System & Software Updates: Why you shouldn’t be skipping them for later
We all know how annoying it can be when you get a pop-up asking if you’d like to update something or—worse still—your system suddenly starts to update itself. Inevitably it happens when you’re on an important call or when you must reply to an urgent email. There is...