Blog
How Privileged Access Management (PAM) Protects Hybrid Organizations
The cost savings, speed, and productivity of the cloud is attracting more and more small businesses. This is leading to a huge rise in hybrid infrastructures, meaning a combination of both virtual and in-house technologies (like an in-house server to run Quickbooks,...
5 Ways to Minimize Data Loss
Our personal and professional data is everywhere. Honestly, that’s how 99.9% of us want it to be. We want our bank account information to auto-populate when we buy things online. We don’t want to have to remember 87 passwords. And we definitely want to be able to see...
5 Stats on Why IT Modernization Pays Off
Innovative technologies are changing the world (and business). Since most businesses pushed to more virtual ways of doing business in the past few years, more and more stats linking business success to technology are being released. The data shows plainly that...
Why All Small Businesses Need a Website Even if They Have a Facebook Page
Yeah, we said it, “…all small businesses need a website.” To get straight to the point, this certainty has nothing to do with selling and everything to do with ensuring the longevity of your company. As an IT partner for small businesses (that in fact, doesn’t service...
What’s the Difference Between a Help Desk and NOC?
When a small business starts outgrowing their piecemealed IT, they often start looking at one facet of technology support, like how to keep their machines secure or how to provide on-demand support for their end users. It’s important to know that one can’t be provided...
Multi-Factor Authentication: The Right Way and the Wrong Way
The IT buzz has a new focus based on all of the increased cybersecurity risk that’s flooding small businesses: multi-factor authentication (MFA) or 2-factor authentication (2FA). They’re slightly different ways of naming the same security requirement that demands a...
Russia-Ukraine Cyberwar Impacts to US Small Businesses
As most these days know, Ukraine has been subjected to relentless Russian cyber attacks since at least 2013. But the attacks that were hitting it last month were different because they foreshadowed the full-scale military invasion that Russia launched against its...
Small Businesses Cybersecurity Breaches Increased in 2021
Small business owners rarely have as much time as they would like, so they must prioritize what they focus on. Given that 56 percent of America’s small business owners are not concerned about being the victim of a hack, it’s hardly a surprise that cybersecurity is...
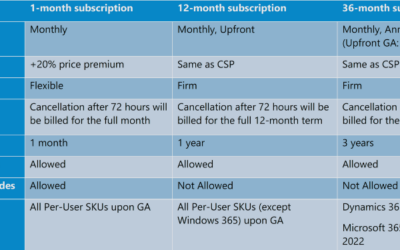
Microsoft’s License Price Increases in 2022: New Commerce Experience (NCE)
DISCLAIMER – All information in this piece is accurate as of the writing of this article and contains no legal advice in terms of purchasing or agreements. This is offered as helpful information to guide our clients and other companies who own and use Microsoft/Office...
Managed IT Services ROI: How Long Does It Take to Start Saving Money?
Are you tired of throwing piles of money on your in-house IT support and feeling like you’re not getting much in return? Fortunately, the remedy is a trend that’s quickly increasing for small businesses: managed IT services. Managed Service Providers, or MSPs for...
How Attacks on Critical Infrastructure Impact Small Businesses
When most small businesses think about cybersecurity, they’re thinking about preventing the bad guys from breaching their defenses, infecting devices with malware, and leaving with sensitive data that’s guaranteed to sell well on the dark web. What small businesses...
4 Things that Will Ensure Your Business Continuity Planning Is a Success
After reading our past articles on What is Business Continuity Planning and Why it’s Essential or Essentials of a Successful Business Continuity Plan, you may be wondering, “How do I make sure what I’m creating actually works?” This article digs into the main four...
The ROI of Moving a Small Business to the Cloud
It’s official. The Cloud is now mainstream and the ROI of moving a small business to the Cloud is only increasing. The number of companies adopting it as their core IT strategy is only going up, and that includes the number of small businesses alongside mid-market and...
Essentials of a Successful Business Continuity Plan
In last week’s blog on ‘What is Business Continuity Planning and Why it’s Essential’, we looked at why a successful business continuity plan is essential, what it is, and a quick look at how to build it. Now we’ll dig into the essential elements of creating a plan...
What is Business Continuity Planning and Why it’s Essential
Whether they liked it or not, most companies received a crash course in business continuity planning in the last few years. From social unrest to the pandemic, businesses who didn’t previously have an eye on their technological stability became quickly aware of it...
Tips on How to Identify an Email Phishing Scam
Even with all the media and information floating the web, did you know that over half of all users end up opening fake emails? And many even fall for them? Think of the person you work closest with at your company. One of you is likely not going to open one in the...
3 Innovative Ideas That Can Increase Your Data Security
Cybercriminals are constantly innovating their tactics and tools to breach yesterday’s defenses. That’s a huge problem because organizations today work with more customer data than ever before. A single data breach can not only bring productivity to a halt, but it can...
Keep Your IT Guy and Outsource IT Services Too
Most companies who start out with an in-house “IT guy” eventually wind up with two paths in front of them: invest in the talent and infrastructure needed to build out their own IT department or outsource some of the IT services that are essential the company’s...
Weighing the Pros and Cons of Working from Home
The pandemic has had many unexpected consequences, from the great toilet paper shortage to the return of endangered Ganges dolphins to the ghats of Kolkata. One that businesses hear about (and experience) regularly is the sudden move to remote work, which is still...
Why You Need to Keep Employee Mobile Devices Updated
What’s the first thing the average employee reaches for when they wake up in the morning? Shockingly, it’s probably not coffee. It’s their smartphone. Due to the fact that this little hand-held computer can let you do almost anything online (including work items),...
10 Email Security Facts that Reveal the Truth About Email Threats
For most small businesses, email is the most valuable tool they have, providing a direct connection between them and their customers. The problem is that this connection is open to anyone who has an interest in exploiting communications to get to sensitive data or...
How to Protect Yourself from the Dark Web
The Dark Web is not an ‘old wives’ tale’ or a story made up by the IT industry to sell more services. It’s a real online world that’s essentially a marketplace for cyber criminals. If they get their hands on stolen data, the Dark Web is the online ‘underground’ where...
7 Things Your Website Must Have
First, do you have a website? If the answer is “yes” then great, move to the information below. If it’s “no,” then stop reading and go talk to a hosting provider right now. In the digital age, it’s imperative (this word can’t be stressed enough) that you have a...
Benefits of Using VoIP Phones Over Landline and Cellular Phones
In a world that’s increasingly more connected, missing a phone call or not looping in an important employee or staff member into a conversation can be trouble for any small business. Add to that the need to keep overhead costs down, and it’s easy to understand why...