
Aug 23, 2021 | Uncategorized
Even if your company has already adopted remote work (or hybrid work, as in some on-site and some remote) as a standard method, this question has probably crossed your mind. Maybe it still is. Kudos to you and your team for taking the security risks seriously and for...

Aug 16, 2021 | Cybersecurity
Not that long ago, you would be happy if your mobile phone had enough memory to store 100 contacts, and you would be ecstatic if it could also store the same number of text messages. Today, your smartphone can not only store a virtually infinite number of contacts and...

Aug 6, 2021 | IT Operations
Modern organizations need their technology to be just that: modern. And that also means that they need modern ways of working to be productive and competitive. Last year’s work routine upheaval (hello, barking dogs and curious toddlers) led to pretty much everyone...
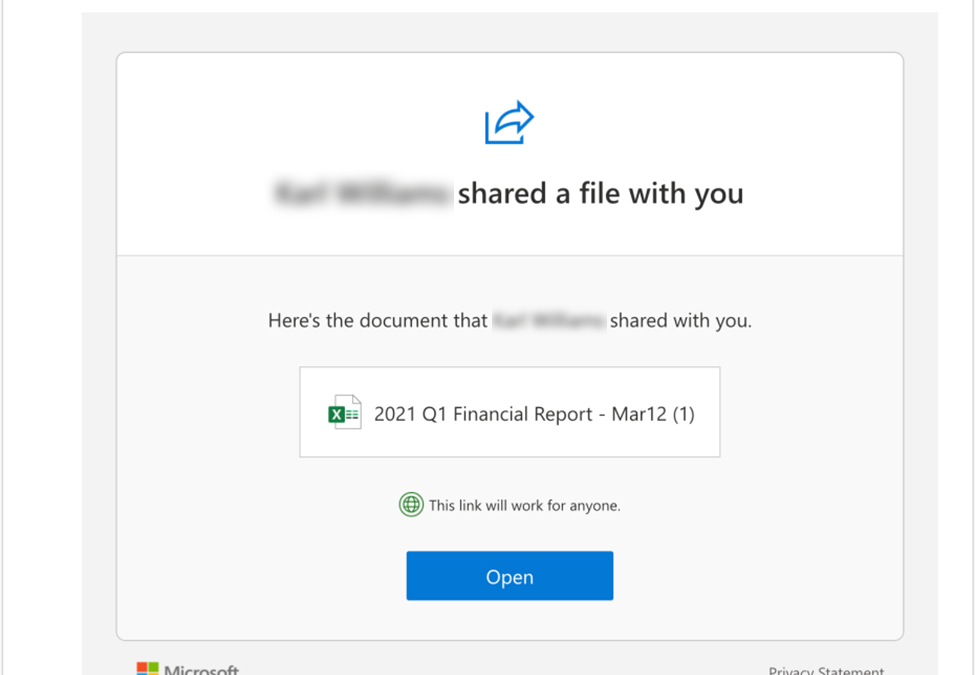
Aug 2, 2021 | Phishing & Scams
A new phishing method has recently been identified and is now on the rise. And because of its well-crafted mimicking abilities, it’s hitting small business end users at an increasing rate. Consent phishing is a new technique that attackers are using in response to the...

Jul 27, 2021 | Cybersecurity
Of all the cybersecurity tools, tricks, software, and processes, none is more important than employee training. It must always be at the heart of your cybersecurity plan. That’s because no amount of cutting-edge technology can protect you from the one thing that is...






