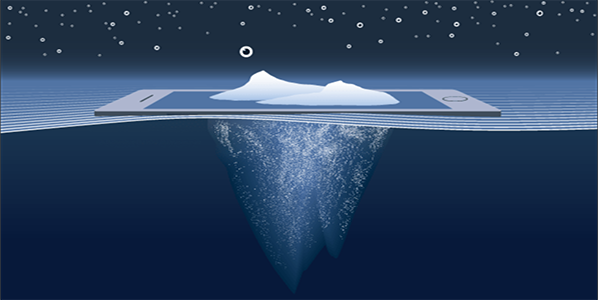
From time to time, the news shouts about some company that had their data security breached and warns consumers that their information may have been leaked. But leaked where? Who wants the information and how do they get it? There are assorted answers to these questions, but one of the most common is: online.
Deep and dark? Is there a difference? Yes, there actually is. Many people mistakenly interchange the two when they’re referring to a amorphous place that data thieves go to sell information. When in reality, the deep web and the dark web are very different and while the dark web has some scariness to it, they are both arenas for completely legal activities. Let’s break it down.
The World Wide Web (aka The Clear Web)
 This is the internet world that the majority of us live and play on throughout our days. It holds all of the publicly accessible websites and their content. That means everything that your Google or Bing search finds for you as well as all of the social media content (that hasn’t been shielded due to privacy settings) and advertising. The surprise here is that this is actually the smallest part of the web. It’s particularly shocking when you think about how many search results you get on a daily basis. That’s because the majority of the content lies within…
This is the internet world that the majority of us live and play on throughout our days. It holds all of the publicly accessible websites and their content. That means everything that your Google or Bing search finds for you as well as all of the social media content (that hasn’t been shielded due to privacy settings) and advertising. The surprise here is that this is actually the smallest part of the web. It’s particularly shocking when you think about how many search results you get on a daily basis. That’s because the majority of the content lies within…
The Deep Web
Totally legal and often misunderstood, The Deep Web holds all of the data that isn’t accessible by the casual surfer or web crawler. To perhaps oversimplify it a bit, it requires that you know the URL (because it won’t surface in search results) or that you log into a gated website to view and interact with its content (like your online medical records or banking information). When you consider how many people and how many companies there are in the world that have essential and private information online, it’s not such a surprise anymore. The Deep Web is considered ethically neutral, but it obviously has some potential for holding illegal activities and information. It’s still discoverable by law enforcement however, so that’s why criminals use…
The Dark Web
What it actually is
Incredibly high security allows users to be completely anonymous (though that’s debatable since authorities work to bring down big Dark Web kingpins like the Silk Road, but that’s for another article), which is why it’s the perfect place for both legal and illegal activities. For activities to be truly anonymous, sites must be accessed by a highly secure browser such as the Tor onion router which masks the user from any tracking processes.
It also requires that you know the URL down to the last hyphen since there are no crawlers shooting you a discovered or suggested site. For instance, maybe you want to open YouTube, so you type “youtub” in your Google address bar. Google is more than happy to suggest Youtube.com as you type, and if you hit Enter, it will be your first search result. This is impossible for any content that’s created for The Dark Web. So, criminals don’t just download the Tor browser and then start searching for “stolen company data.” They have a network of shared information that includes the URLs they need to visit in order to find or sell their wares.
The legal aspects
It’s hard to know if The Dark Web was first created to house legal organizations and activities or if the scary criminals started it to cloak their actions. Either way, there are legal sites that span award winning whistle blowers (like WikiLeaks) to small first amendment activist organizations. For many reasons, users do not want to be identified so The Dark Web is a natural place for them to organize and disseminate information.
The illegal aspects
This is what the news is shouting about and where stolen data is moved around like the gold watch hidden in the pocket of a hoodie. It’s also home to uncountable other illegal sales like weaponry, blueprints, drugs, and even hiring hitmen. For anyone who knows the URL to type in their secure browser, these sites are hubs for trafficking just about anything: your banking information, passwords, and personal data that can give social engineering attackers an easier time earning your trust.
What You Can Do
Get a Dark Web Report
With just your company’s domain, a search can surface any data that might be floating around on The Dark Web. Since a single company can have thousands of passwords and various banking accounts, it’s important to run a report on a regular cadence so you can change the most vital information first. There are many services out there, and as an HDCav client, you’ll have access to regular, free reports. Contact us if you’re interested in one.
Watch your finances
Sounds like common sense, right? But it’s far too easy for a busy company owner or part-time bookkeeper to procrastinate this kind of oversight task. Criminals don’t always go for a giant, single payout since they know your bank may flag it as fraud. If an attacker manages to get your banking information, they may scan your recurring charges and find ways to sneak in similar ones that are easy to overlook. Keep those company credit cards on tight leashes and make sure you have a bookkeeper or accounting professional that you trust to watch the details.
Get a serious password manager and protocol in place
Password hacking tools exist (there are actually quite a few) and attackers use them. And just like all technology, they’re only advancing as time goes by. Make sure your security protocols encompass secure password practices and require that anyone using company assets or accessing company data must use your official password management tool. Don’t have one? That’s something you need now. Contact us so we can get security protocols created and implemented for your company.
Get phishing training for you and your team
You can’t do this soon enough. If you’ve read this far, then you obviously understand that there are real threats out there. But what about the people you work with? People take the gravity of these risks very differently. The only way to level the playing field is to require each employee go through phishing training which educates them then tests their ability to spot scams and frauds. It even scores each person so they can try for a better result if it turns out they don’t equal company standards. Phishing tests are relatively quick and painless and innately intertwine with regular work activities, so they’re less disruptive. And we find that a company’s overall acumen increases dramatically after just one round. That’s because many people just need awareness in the first place. And yes, we provide phishing training and testing as well. Contact us to set it up.
It’s Not Going Anywhere
The Dark Web is here to stay which means that companies who educated and take the possible threats seriously will have a leg-up on their competition. Kudos on making it all the way through this article, and you might also find these other pieces helpful:
10 Major Types of Phishing Scams
How to Detect a Phishing Email
As always, we’re here when you need us. From advanced security planning to a secure place to keep all your passwords, we have everything necessary to keep your company as secure as possible. A quick conversation is all that’s needed for us to know where you need our help. Stay safe out there!