In our last blog, we showcased the most commonly used types of phishing scams like waterholing, whaling, and smishing. Now we want to help you spot them. Most of these scams have tell-tale signs which means that you can proactively train your employees and educate your family about them.
Remember: The first line of defense against a phishing attack is YOU (and your users). While there are measures that can help protect you in case of a successful attack, nothing beats proactively making sure that attacks are as small of a risk as possible. If you’re a Help Desk Cavalry client, we have you covered from the technology side. Now it’s up to you to get your users involved and avoid the little mistakes that cause BIG losses.
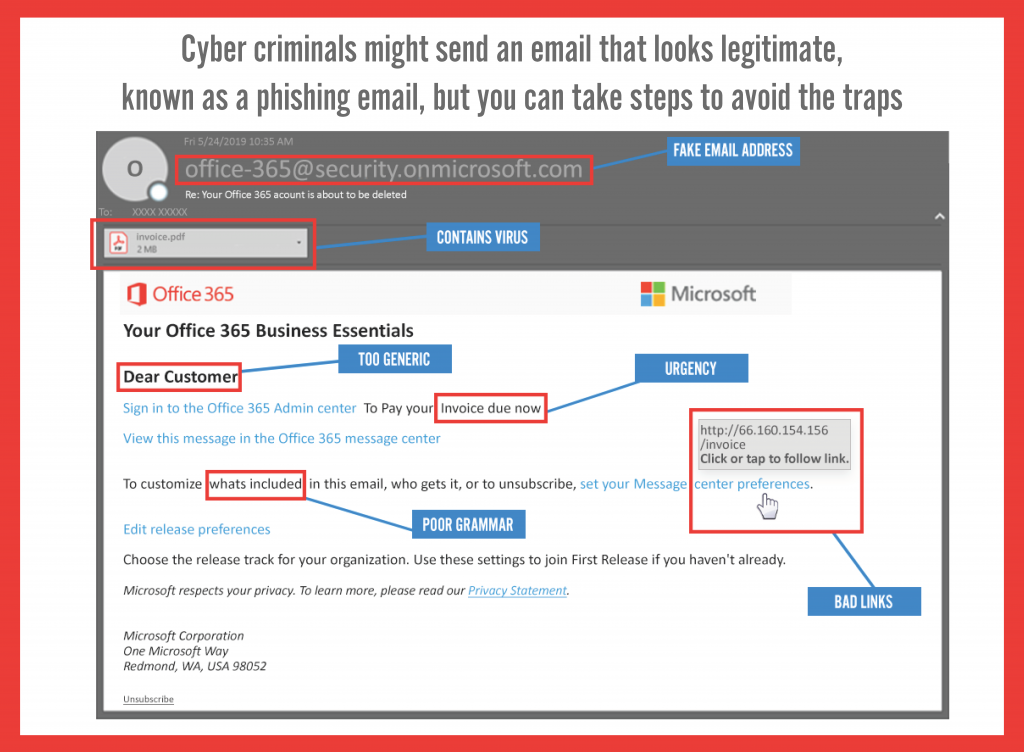
How to Spot the Scam
1. Watch for overly generic greetings and generalized content
Cyber criminals will send a large batch of emails, so they’re trying to appeal to the widest audience they can. Look for greetings like “Dear valued customer.”
2. Examine the entire from email address
The first part of the email address may be legitimate, but the last part might be off by letter or may include a number in the usual domain. This is a sign that domain spoof phishing is being employed.
3. Look for urgency or demanding actions
“You’ve won! Click here to redeem prize,” or “We have your browser history pay now or we are telling your boss.” Remember that if it seems to good to be true, it probably is. And remember that fear can sometimes be the best motivator to take immediate action without thinking through the situation.
4. Carefully check the link before you click
Yeah, this takes time. But since this is the most common way an attacker gets in, it’s worth it. Mouse over the link and see if the links destination matches where the email implies you will be taken.
5. Notice misspellings, incorrect grammar, & odd phrasing
There a lot of reasons for any of the above. It might be a deliberate attempt to bypass spam filters. Or it might be due to an attacker focusing more on the action they’re trying to force and less on the wording. Whatever the case, consider if the sender would really write an email with bad grammar and act accordingly.
6. Check for Secure Websites
Blanket rule: Any webpage where you enter personal information should have a URL with https:// at the beginning. The “s” stands for secure.
Additional Tips to Stay Safe
1. Don’t click on attachments or links
Virus containing attachments might have an intriguing message encouraging you to open them such as “Here is the schedule I promised.” Don’t click on anything until you know the email is legitimate. Links and attachments can lead you to malicious websites or install harmful malware to your device.
2. Contact the source directly
Contact the company or person directly using a phone number or website URL you know is correct. Use a search engine to look up the website or phone number for the company or person who is contacting you. Do not use or click on the information in the email to contact the source.
3. Remember that phishing isn’t limited to email
Even if you successfully identify phishing attempts in your work inbox, it does not mean you are safe from other forms of phishing. Hackers regular compromise social media accounts to send out malicious links, which can be especially dangerous if you use these platforms on your work devices.
4. Cybersecurity awareness training
One of the most effective measures you can take to protect your business and your bottom line is to train your employees and yourself in cybersecurity awareness. Employees that are trained to recognize the signs of phishing attacks become your organization’s best line of defense against cybercriminals.
Of course, if you’re a Help Desk Cavalry client, you’re always welcome to forward any suspicious email to our Help Desk (you know where to send it). Our technicians are experts at spotting risky access points and they can quickly let you know how to deal with one.
If you’re interested in learning more about how our team can help make sure your technology and your users stay safe with evolving phishing threats, just contact Biz@HDCav.com. A quick call can explain a lot.

