
Aug 9, 2022 | Cybersecurity
For small businesses, the most common competitive advantage is their proximity to customers, which allows them to deliver a more personalized customer service experience. But there’s another often-overlooked source of a competitive advantage that small businesses can...

Jul 26, 2022 | Cybersecurity
Personal social media accounts are one of the most common forums for cyberattacks. You may think cybercriminals would prefer to hack online banking accounts or shopping accounts, but that doesn’t seem to be the case. Social media accounts hold a lot of personal...
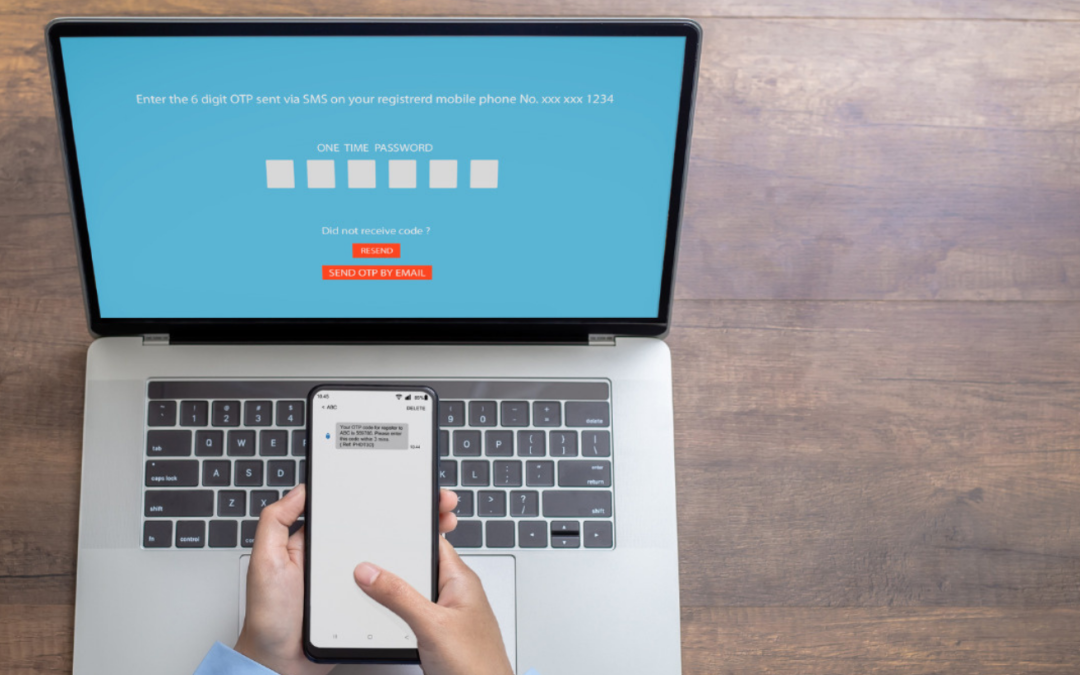
Jul 18, 2022 | Products & Terms
There’s a very good chance that you’re already using multi-factor authentication somewhere in your virtual life. That’s because it’s one of the fastest, cheapest, and most universal way for companies and manufacturers to enforce safety protocols for those logging into...

Jul 11, 2022 | Cybersecurity
Cybersecurity compliance is like a puzzle. To see the big picture for your company, you must place all of the pieces in the right place. The problem is that it’s not immediately obvious how many pieces there are. Unfortunately, regulations aren’t delivered to small...

Jul 5, 2022 | IT Operations
Many small businesses begin with simple basics: a plan for administration, sales, technology, customer service, and maybe some marketing. Of all of these, technology is quickest to change while also carrying the highest risk. As companies grow, though, they often...






